Piracy is an issue for games and other software developers. Some handle it in novel ways, like deliberately making pirated versions of a game near unplayable, or by releasing their software for free. One piece of flight simulator software had an unusual, and controversial technique: infecting pirates with malware designed to steal their Chrome passwords.
“The inclusion of a malware, in the form of a password dumper, in a trusted installer for the sake of combating piracy is absolute insanity,” Andrew Mabbitt, founder of cybersecurity company Fidus Information Security and who originally flagged the issue to Motherboard, said. Kurtis Baron from Fidus also worked on digging through the program.
Videos by VICE
FSLabs makes add-ons for the hyper popular Microsoft Flight Simulator, according to the company’s website. Budding digital pilots can buy the opportunity to fly other aircraft from around $80 and up.
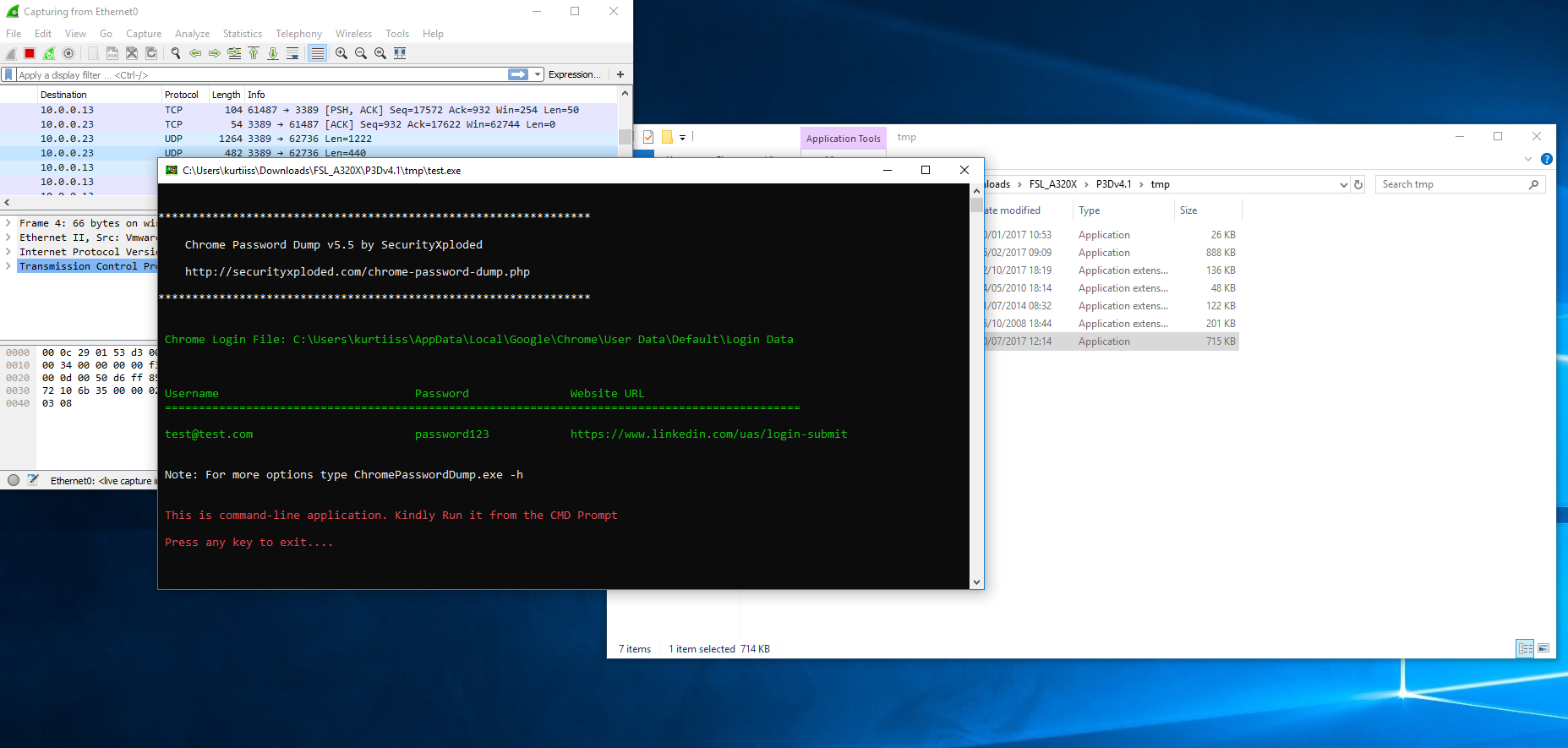
On Sunday, a user of the /r/flightsim subreddit noticed something amiss with FSLabs’ installer for the A320X add-on, a particular model of aircraft. FSLabs’ software also included a file called “text.exe,” which is actually a password stealer, according to the user’s post.
Mabbitt said he verified that the file is included in FSLabs’ installer. Mabbitt also pointed to a scan of the file on malware search engine VirusTotal, which shows a slew of anti-virus products mark the file as malicious.
“When run, the program extracts all saved usernames and passwords from the Chrome browser and appears to send them to FSLabs. This is by far one of the most extreme, and bizarre, methods of Digital Rights Management (DRM) we’ve ever seen,” he added.
Lefteris Kalamaras, founder and owner of FSLabs, took to the flight simulator’s forums on Saturday, and did not deny bundling a piece of malware with his product.
“First of all—there are no tools used to reveal any sensitive information of any customer who has legitimately purchased our products. We all realize that you put a lot of trust in our products and this would be contrary to what we believe,” he wrote; emphasis his own.
“There is a specific method used against specific serial numbers that have been identified as pirate copies and have been making the rounds on ThePirateBay, RuTracker and other such malicious sites,” he added. Often software users need to enter a key or string of characters in order to activate a program. In this case, it appears that if the key was one FSLabs already knew was being used by software pirates, then the password stealer would kick in.
But, the malware file itself, even if not activated, was still “dropped on every single PC it [the FSLabs software] was installed on,” Mabbitt said.
After the publication of this piece, Kalamaras elaborated on the FSLabs forums, and said the bundled software was used to try and catch one particular game pirate.
“We found through the IP addresses tracked that the particular cracker had used Chrome to contact our servers so we decided to capture his information directly – and ONLY his information (obviously, we understand now that people got very upset about this – we’re very sorry once again!) as we had a very good idea of what serial number the cracker used in his efforts,” Kalamaras wrote.
The company has released an updated version of its installer, this time without the password stealer.
“While the majority of our customers understand that the fight against piracy is a difficult and ongoing battle that sometimes requires drastic measures, we realize that a few of you were uncomfortable with this particular method which might be considered to be a bit heavy handed on our part,” Kalamaras wrote on the FSLabs forum on Monday. “It is for this reason we have uploaded an updated installer that does not include the DRM check file in question.
Update: This piece has been updated with additional information from Lefteris Kalamaras’ forum posts.




