The Department of Justice has charged a Deputy U.S. Marshal for allegedly abusing access to a controversial phone tracking service offered by a company called Securus to track the physical location of people he had personal relationships with as well as their spouses.
The news highlights the stark risk of abuse of telecoms’ mishandling of their users’ location data and the for-profit tracking services based on that data. Securus first entered public consciousness when the New York Times and the office of Senator Ron Wyden investigated the service in 2018. The Times showed that a former sheriff leveraged the system for their own use, including monitoring the location of a judge. This latest indictment suggests that abuse was not an isolated incident and that abuse of Securus’ Location Based Services (LBS) product was more widespread.
Videos by VICE
Do you have any more information abuses of location data? We’d love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
Adrian O. Pena used Securus between September 2016 and October 2017 while serving as a Deputy U.S. Marshal, according to the indictment. He did this by uploading fake documents to the Securus platform that he claimed gave him authority to obtain requested location data, the indictment adds.
Pena was assigned to the Lone Star Fugitive Task Force in the Uvalde County Sheriff’s Office in Texas, which had access to the system, according to the indictment. (Uvalde is the city where local police have been widely criticized for their failure to act in a mass shooting at Robb Elementary school in May where 19 children and two adults died).
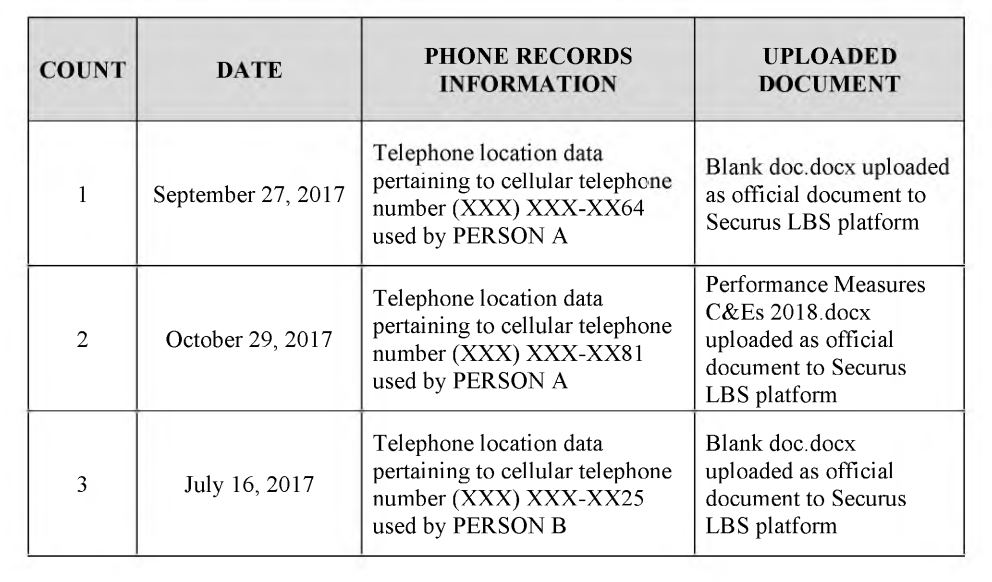
“Pena on numerous occasions used the LBS platform to obtain location data associated with the cellular telephones of his personal associates, including individuals with whom Pena was or had been in a personal relationship and their spouses,” the indictment reads. The indictment includes details on 11 separate alleged violations in which Pena abused access to the system. They relate to nine different people.
After being confronted by law enforcement officials about his actions, Pena allegedly lied about using the Securus service for personal reasons. In a November 2017 interview with the Office of the Inspector General (OIG), which provides oversight of agencies, one OIG official asked Pena “Other than yourself, have you ever pinged anybody using the system? You know, family members, friends, ex-girlfriend?”
“No,” Pena responded. “But there is like lost phones and stuff like that—that a deputy lost a phone and—we’re trying to find his phone and stuff like that.” At one point the OIG official asked if Pena was married, to which he replied yes. The official then asked if Pena ever looked up a high school girlfriend.
“No,” Pena replied.
The indictment doesn’t go into more detail on the specific victims, but at the end of the transcript of the conversation with OIG officials it adds, “These statements and representations were false because, in truth and in fact, and as PENA well knew, PENA had used the Securus LBS platform for personal reasons on numerous occasions, including to obtain cellular telephone location data relating to individuals with whom PENA was or had been in a personal relationship and their spouses.”
Shortly after the interview with OIG officials, Pena drafted a statement for one of his victims to sign that falsely said she had provided Pena with permission to track her phone at all times since 2012, the indictment adds. That included all her social media data, call history, text messages, and cell phone location data “24/7-365” “without any restrictions,” the indictment reads.
Securus is a massive prison and law enforcement contractor that, among many other things, previously offered a service for geolocating nearly all phones in the United States called Location Based Services. This was facilitated by a continuous relationship with a location data broker called 3Cinteractive Corporation, which in turn obtained access to the data from another broker called LocationSmart. AT&T, T-Mobile, Sprint, and Verizon sold the access to their own users’ location data to LocationSmart as part of a convoluted supply chain of data that most phone users likely had no idea existed. The system provided users with a handy map interface of where their target was approximately located.
Securus said it only offered the location service to law enforcement officials. During its operation users were asked to upload a document, such as a search warrant or other legal mechanism, and tick a box saying that the document gave them permission to lookup the requested location data. In 2018, Senator Wyden described this process as little more than a “pinky promise.”
Indeed, some of the documents Pena allegedly uploaded were simply blank pages, award certificates, and letterhead templates, according to the indictment. A table in the indictment lays out more specifics for each alleged violation, including the document uploaded.
“Blank doc.docx uploaded as official document to Securus LBS platform,” eight of the 11 instances read.
“These documents were not official and did not provide PENA with permission to obtain cellular telephone location data from Securus,” the indictment adds.
Responding to the news of the indictment, Senator Wyden reiterated the lax security measures in place at Securus and told Motherboard in an emailed statement that “When Securus gave law enforcement essentially unrestricted access to track any phone in the country, it was inevitable the system would be abused. Requiring a pinky promise of a court order was woefully insufficient, as this case demonstrates.”
At the time of the Times’ and Senator Wyden’s investigations into Securus, the telecoms said they would stop selling users’ location data. A year later, Motherboard published a wave of stories showing not only that AT&T, T-Mobile, and Sprint continued to share such information, but that it was being sold to bounty hunters and other third parties. After those revelations, the telecoms finally stopped the data selling program.
Securus told Motherboard in a statement that “Privacy and security are fundamental and we support efforts to ensure individual data is protected. We discontinued the tool more than four years ago and permanently shut it off. Even when operable, it was only available to users who were granted authorization by a law enforcement agency or facility. The tool was engineered with safeguards and security protocols, but we also relied on the integrity of law enforcement to operate it ethically. All of this preceded our aggressive, multi-year transformation, and we wouldn’t and won’t provide the service ever again, period.”
Dave Oney from the U.S. Marshals’ Office of Public Affairs told Motherboard in a statement that “The U.S. Marshals Service is aware of the indictment of Deputy U.S. Marshal Adrian Pena. We are cooperating fully with the Department of Justice Office of Inspector General’s investigation of the matter. We take seriously any allegation of misconduct by our personnel. The alleged actions of this employee do not reflect the core values of the U.S. Marshals Service, and Pena has been relieved of his operational duties and placed on administrative leave. An indictment is merely an allegation, and the defendant is presumed innocent until proven guilty beyond a reasonable doubt in a court of law.”
In May 2018, Motherboard reported that a hacker broke into servers belonging to Securus and stole data including usernames and poorly secured passwords.
Motherboard has also revealed how stalkers have posed as U.S. Marshals to convince telecoms to provide them with real-time location data of victim’s phones. One victim previously told Motherboard that T-Mobile put her “life in danger.”
Update: This piece has been updated to include statements from Senator Ron Wyden, Securus. and the U.S. Marshals.
Subscribe to our cybersecurity podcast, CYBER. Subscribe to our new Twitch channel.






