The sleek, black phone seems perfectly normal.
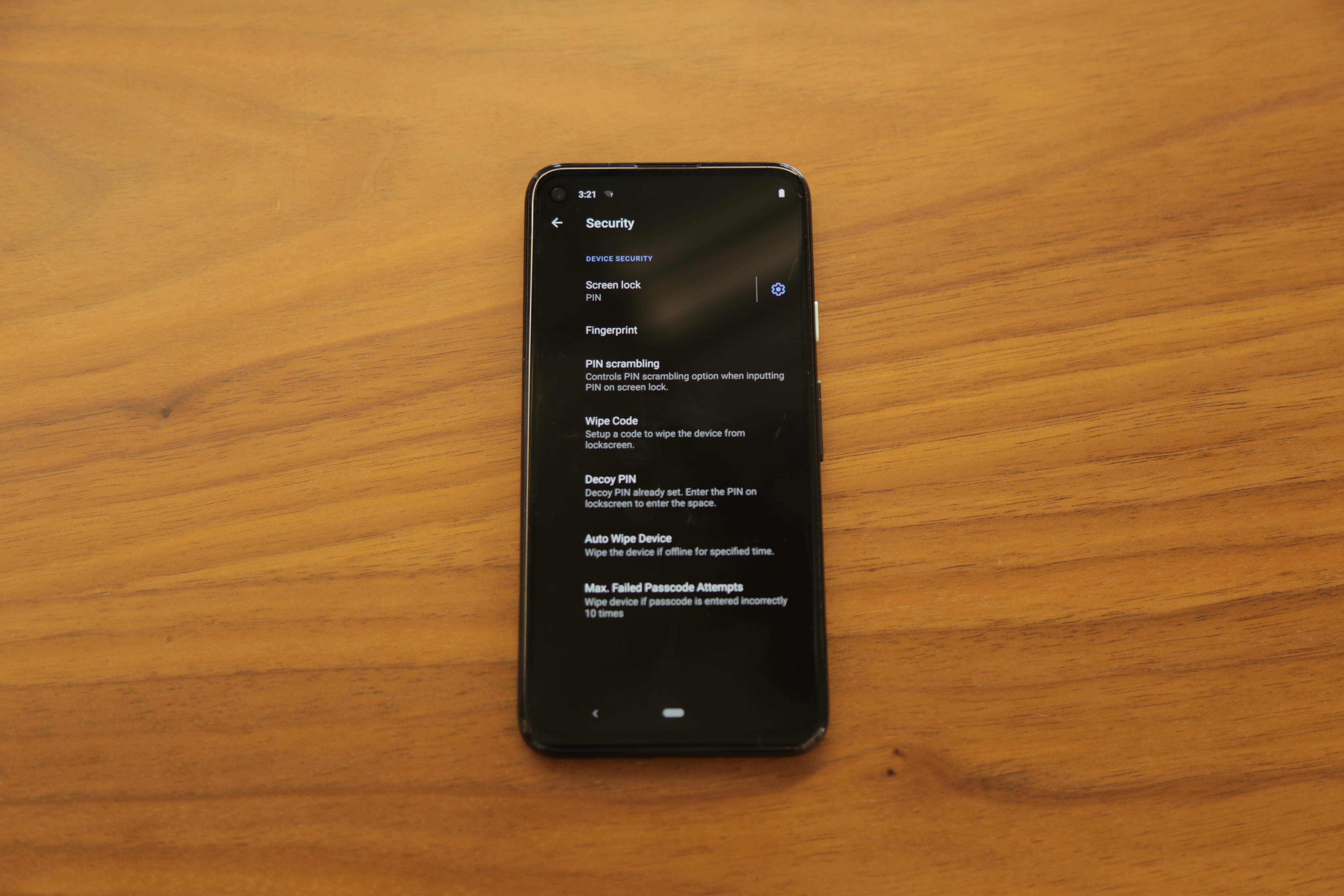
Unlocking the Google Pixel 4a with a PIN code reveals some common apps: Tinder, Instagram, Facebook, Netflix, and even Candy Crush. But none of those apps work, and tapping their icons doesn’t do anything. Resetting the phone and typing in another PIN opens up an entirely different section of the device, with a new background and new apps. Now in place of the old apps sit a clock, a calculator, and the device’s settings.
Videos by VICE
Clicking the calculator doesn’t open a calculator—it opens a login screen.
“Enter Anom ID” and a password, the screen reads. Hidden in the calculator is a concealed messaging app called Anom, which last month we learned was an FBI honeypot. On Anom, criminals believed they could communicate securely, with the app encrypting their messages. They were wrong: an international group of law enforcement agencies including the FBI were monitoring their messages and announced hundreds of arrests last month. International authorities have held press conferences to tout the operation’s success, but have provided few details on how the phones actually functioned.
Motherboard has obtained and analyzed an Anom phone from a source who unknowingly bought one on a classified ads site. On that site, the phone was advertised as just a cheap Android device. But when the person received it, they realized it wasn’t an ordinary phone, and after being contacted by Motherboard, found that it contained the secret Anom app.
The person Motherboard bought the phone from said they panicked “when I realised what I had just purchased.” Motherboard granted the person anonymity to protect them from any retaliation.
Do you know anything else about Anom? Were you a user? Did you work for the company? Did you work on the investigation? We’d love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
When booting up the phone, it displays a logo for an operating system called “ArcaneOS.” Very little information is publicly available on ArcaneOS. It’s this detail that has helped lead several people who have ended up with Anom phones to realize something was unusual about their device. Most posts online discussing the operating system appear to be written by people who have recently inadvertently bought an Anom device, and found it doesn’t work like an ordinary phone. After the FBI announced the Anom operation, some Anom users have scrambled to get rid of their device, including selling it to unsuspecting people online. The person Motherboard obtained the phone from was in Australia, where authorities initially spread the Anom devices as a pilot before expanding into other countries. They said they contacted the Australian Federal Police (AFP) in case the phone or the person who sold it was of interest to them; when the AFP didn’t follow up, the person agreed to sell the phone to Motherboard for the same price they paid. They said they originally bought it from a site similar to Craigslist.
Another person Motherboard spoke to who bought one of the phones said they were in Lithuania.
“I bought this phone online, for ridiculously low price, now I understand why,” that second person said. That person also provided Motherboard with photos and a video of their device. In that case, the Anom login screen appeared inaccessible, but other settings such as the decoy PIN code remained. “Probably this phone was used by some drug dealer :D,” they said.
For the past few months, members of Android hobbyist and developer forums have been trying to help the people who bought the strange phones return them to a usable state.
“I cannot install any apps because there is no [App Store], everything has been removed,” one person who said they bought the phone second-hand wrote on a German language forum in March, before the FBI and its partners stopped the operation.
“If he also had access to/data, he could change all of the cell phone’s settings manually,” one forum user replied.

“That’s strange… You have the boot screen saying that the phone has been modified, yet you seem to have a locked bootloader… Doesn’t make any sense to me :/,” a user on another forum replied to someone facing similar issues.
“I have the same thing. A friend got a used pixel 4a and it’s running arcaneos with the same issues described by the OP. Nothing works when attempting to flash,” someone else added to the thread.
After Motherboard determined that ArcaneOS was linked to the Anom devices and had bought the phone, someone else on one of the forums also made the connection.
“This is a phone the used with that FBI ANON [sic] application to read the message with the users,” a user wrote on a thread. That user did not respond to a request for comment on how they also came to the same conclusion.
The Phone
Besides ArcaneOS, the phone has a few other interesting features and settings.
Ordinarily, Android phones have a setting to turn location tracking off or on. There appears to be no setting for either on this device.
The phone offers “PIN scrambling,” where the PIN entry screen will randomly rearrange the digits, potentially stopping third-parties from figuring out the device’s passcode if watching someone type it in. The status bar at the top of the screen includes a shortcut for what appears to be a wipe feature on the phone, with an icon showing a piece of paper going through a shredder. Users can also set up a “wipe code,” which will wipe the device from the lockscreen, and configure the phone to automatically wipe if left offline for a specific period of time, according to the phone’s settings reviewed by Motherboard.
Encrypted phone companies typically offer similar data destruction capabilities, and at least in some cases companies have remotely wiped phones while they’re in authorities’ possession, hindering investigations. The Department of Justice has charged multiple people who allegedly worked for Anom in part for obstructing law enforcement by using this wipe feature.
Daniel Micay, lead developer of security and privacy focused Android operating system GrapheneOS, also provided Motherboard with images someone had recently sent him of a third Anom device. That phone was a Google Pixel 3a, suggesting Anom loaded its software onto multiple iterations of phones over time, and the Anom login screen was not immediately accessible.
“The calculator theoretically opens chat but it doesn’t work anymore. They said it requires entering a specific calculation,” Micay said. “Quite amusing security theater.”


Micay said others claimed that Anom used GrapheneOS itself, but “it sounds like they may have advertised it to some people by saying it uses GrapheneOS but it has no basis.”
“Basically [it] sounds like people have heard of GrapheneOS so these companies either use it in some way (maybe actual GrapheneOS, maybe a fork) or just claim they did when they didn’t,” he said.
The phone obtained by Motherboard and the one included in the video both have an identical list of contacts saved to the innocuous looking section of the device. However, at least some of these appear to be placeholder contacts generated by a specific tool available on Github. None of the people included in the contact list responded to a request for comment.
With its wipe features and the hidden user interface, the Anom device does look like one from any of the other encrypted phone firms that serious organized criminals have used in the past, such as Encrochat and Phantom Secure. That was very much on purpose, according to Andrew Young, a partner in the Litigation Department in law firm Barnes & Thornburg’s San Diego office and former Department of Justice lead prosecutor on the Anom case.
“We can’t just run a good investigation; we have to run a good company,” he previously told Motherboard in a phone call. That included providing customer service and solving users’ tech issues, and potentially dealing with hackers who may target the company too.
Anom started when an FBI confidential human source (CHS), who had previously sold devices from Phantom Secure and another firm called Sky Global, was developing their own product. The CHS then “offered this next generation device, named ‘Anom,’ to the FBI to use in ongoing and new investigations,” court documents read.
In June the FBI and its law enforcement partners in Australia and Europe announced over 800 arrests after they had surreptitiously been listening in on Anom users’ messages for years. In all, authorities obtained over 27 million messages from over 11,800 devices running the Anom software in more than 100 countries by silently adding an extra encryption key which allowed agencies to read a copy of the messages. People allegedly smuggling cocaine hidden inside cans of tuna, hollowed out pineapples, and even diplomatic pouches all used Anom to coordinate their large-scale trafficking operations, according to court documents.
The FBI declined to comment.
Subscribe to our cybersecurity podcast, CYBER.




