A few years ago, Dan Guido’s partner couldn’t log into her bank account via the bank’s official iPhone app. The app kept alerting her that her phone was not secure.
“Being a security guy, I freaked out,” said Guido, who is the founder of the cybersecurity research firm Trail of Bits.
Videos by VICE
The bank’s app, it turned out, was designed to detect iPhone hacks, but the detection code was buggy and “total garbage,” according to Guido. That’s when he and his colleagues decided to create a better tool to detect iPhone jailbreaks and hacks.
For years, there’s been no real way to know whether your iPhone had been hacked. Guido is hoping to change that.
The tool he made, called iVerify, is now on the iPhone App Store—one of the first ever apps that promises to catch iPhone hacks to be approved to be on the official App Store.
iPhones are widely believed to be some of the most secure devices one can get. But in the last few months, security researchers have shown the cracks on the iPhone’s garden walls. Over the summer, a Google researcher found 10 critical bugs in iMessage that would have allowed hackers to silently and stealthily take over an iPhone. Then, a few weeks later, Google revealed that hackers—reportedly working for the Chinese government—had been using unknown iPhone vulnerabilities to target the phones of Uighurs, a Muslim minority group in China that has faced arbitrary detentions and repression for years.
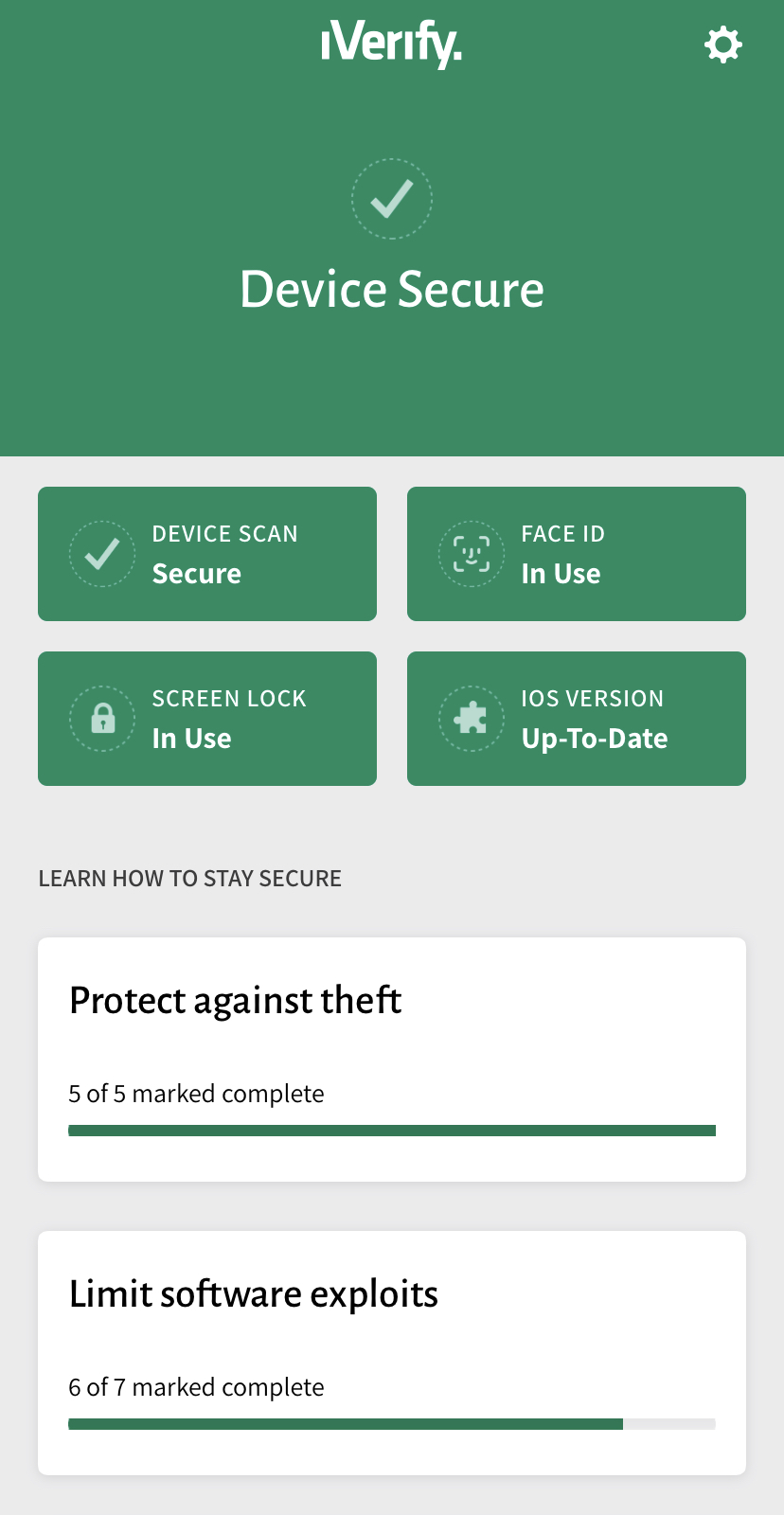
iVerify is designed to look for “side effects” or anomalies created by iPhone hacks or jailbreaks, according to Ryan Stortz, a security researcher that focuses on iOS at Trail of Bits. This, according to Guido, is the “secret sauce” of iVerify and is based on studying all existing past public jailbreaks and reverse engineering the iPhone’s operating system.
“The jailbreak detection is using side channels to figure out information outside of the sandbox. This is like sending up smoke signals out and you’re looking at the clouds in the sky through a tiny little window in your room where you’ve been locked,” Guido explained. “And you can read a message about what’s going on in the outside world. That’s how jailbreak detection works. We found a lot of different signals that are present in the environment that gives us an indication of what’s really going on on the phone.”
The iPhone, however, is designed in a way that limits the kind of data tools like iVerify—like any other app—can get access to. That’s why some security researchers have complained in the past that it’s almost impossible to figure out if your iPhone was hacked.
“We’re playing a losing game because of the way the platform is set up,” Guido said, referring to the restrictions that Apple has put in place for apps on the iPhone, such as sandboxing them and making it hard for apps to collect user data. “But that doesn’t mean we shouldn’t try.”
Do you work or used to work at Apple? We’d love to hear from you. Using a non-work phone or computer, you can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzofb@vice.com
Apple did not respond to a request for comment.
iVerify is not the first app that promises to catch iPhone attacks. In 2016, a well-known iPhone security researcher released a similar tool, but it was quickly banned from the App Store. Guido and Stortz claim that iVerify is more advanced than that app.
Moreover, iVerify is not just a hacking detection tool, it also includes a series of detailed how-to guides that help users lock down their iPhone settings to improve their privacy and reduce the chances of getting hacked. This is not a “download it and forget it” app. You need to work with the app and follow its instructions and recommendations.
That’s great because it teaches you what to do, and you learn what you should be worried about—or not worried about—and how to protect yourself.
“iVerify definitely highlights some of the more impactful, yet lesser-known, tips to harden an iPhone. And I can doubly appreciate how clear its instructions for implementing those tips are,” said Harlo Holmes, a digital security trainer who works at the Freedom of The Press Foundation.
Holmes specifically pointed out to iVerify’s advice to turn off Javascript, a popular vector to attack users, as a very useful—albeit extreme—measure to reduce the chances of getting hacked.
“It might be a bridge too far for the average user, but for those with higher threat profiles, that’s a great hardening step to take,” she said.
Leigh Honeywell, the CEO of the anti-harassment startup Tall Poppy, who has used iVerify, agreed that it’s a very useful tool for people at risk.
“In working with targets of online harassment and abuse, people are often concerned that their devices are compromised and being used to track them,” Honeywell said in an online chat. “Being able to point vulnerable users at a tool like iVerify lets me help people start feeling safe again.”
It’s important to point out that when stalkers want to keep tabs on victims using iOS, they usually abuse normally harmless features like Find My iPhone or Google Maps’s share location feature, as opposed to hacking the phone, Honeywell noted. “But being able to rule out deeper [operating system] compromises lets us quickly eliminate a whole category of threats,” she said.
In the event that an iVerify user does get hacked, the app alerts them, then creates a personalized URL that includes data on what was detected and what went wrong. The app also gives the user some basic advice on what to do next, and sends the incident report to Trail of Bits.

Getting iVerify on the app store wasn’t easy, and took a few weeks of back and forth between Apple and Trail of Bits engineers. The main complaint from Apple was that the app recommended specific apps to improve users’ security, such as the password manager 1Password, the two-factor apps Google Authenticator and Authy, and the encrypted messaging app Signal, among other apps. Apple told Trail of Bits that recommending specific apps goes against the App Store’s terms of service. (Apple also did not allow iVerify to be on the Chinese App Store because it also recommends VPNs, which are illegal in China.)
iVerify costs $4.99, and Trail of Bits also plans to license the underlying jailbreak detection tech, known as iVerify Core, to companies who want to integrate it in their products or customize it for their own employees.
Guido hopes that with enough users, Trail of Bits will be able to catch attacks in the wild, and protect people from hackers.
“There’s a chance that we’re going to catch a whole lot of people by surprise,” Guido said, while admitting that it’s not going to be a silver bullet.
“The app does a good job of explaining how to keep your device as safe as possible for the average person,” Holmes told me. “That said, no app is going to protect you from the unknown.”
Subscribe to our new cybersecurity podcast, CYBER.
More
From VICE
-

Photo by Marcel van Dorst/NurPhoto/Shutterstock. -

-

-

