A mysterious piece of malware has been infecting hundreds of Mac computers for years—and no one noticed until a few months ago.
Earlier this year, an ex-NSA hacker started looking into a piece of malware he described to me as “unique” and “intriguing.” It was a slightly different strain of a malware discovered on four computers earlier this year by security firm Malwarebytes, known as “FruitFly.”
Videos by VICE
This first strain had researchers scratching their heads. On the surface, the malware seemed “simplistic.” It was programmed mainly to surreptitiously monitor victims through their webcams, capture their screens, and log keystrokes. But, strangely, it went undetected since at least 2015. There was no indication of who could be behind it, and it contained “ancient” functions and “rudimentary” remote control capabilities, Malwarebytes’s Thomas Reed wrote at the time.
Read more: The Life, Death, and Legacy of iPhone Jailbreaking
The second version of FruitFly is even more puzzling, according to Patrick Wardle, the former spy agency hacker who now develops free security tools for Apple computers and researches Mac security for the firm Synack. Wardle told Motherboard in a phone call that when he first discovered FruitFly 2, no anti-virus software detected it. More surprisingly, it looks like it has been lurking around for five or 10 years and infected several hundred users.
FruitFly and FruitFly 2 are also mysterious: Neither Reed nor Wardle know its mechanism of infection—whether it takes advantage of a flaw in MacOS’s code, is installed via social engineering, or some other way. For that reason, and because Apple didn’t respond to several requests for comment, we’re not sure if computers are still at risk. There may be more than just hundreds of victims because Malwarebytes had limited visibility into FruitFly 1, and Wardle said he likely saw only a portion of infected computers by FruitFly 2.
“This year we’ve seen more Mac malware than in any previous year.”
While FruitFly itself isn’t that sophisticated or advanced, its long, undisturbed life shows that despite the widespread belief that they are virus-free, Macs aren’t immune from invasive and dangerous malware.
“This year we’ve seen more Mac malware than in any previous year,” Reed, the researcher at Malwarebytes who first analyzed the other version of FruitFly, told Motherboard.
TAKING APART FRUITFLY
Frustrated by the long and tedious process of picking it apart —”analyzing malware is kind of a pain in the ass,” he joked—Wardle figured he could just trick FruitFly 2 into telling him what it was after. He discovered that FruitFly 2 was programmed to send data back to the hacker or hackers controlling it—whoever they might be—through a series of backup servers in case the main ones were down. This turned out to be the case, so he registered these backup domains and infected his own virtual machine with FruitFly.
“I was quickly able to fully determine all the malware’s capabilities by basically just asking it the right questions,” Wardle said.
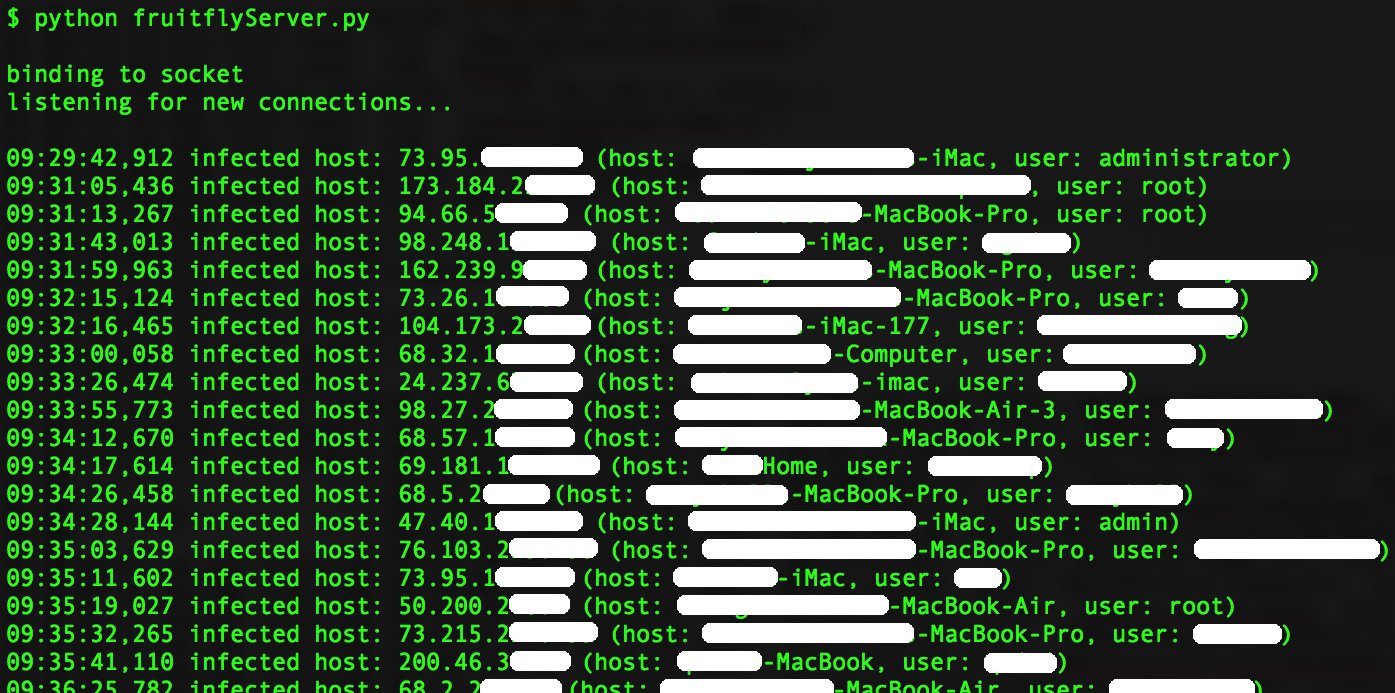
Taking control of a command and control server, however, had another unexpected outcome: Around 400 victims infected with FruitFly started connecting to it. Wardle could have taken over those computers or spied on them if he wanted to. Instead, he warned law enforcement, which is now apparently investigating the case.
An FBI spokesperson told Motherboard that “as a matter of longstanding policy, the FBI neither confirms nor denies the existence of investigations.” Reed told me that Apple told him after he reported FruitFly 1 that the FBI was investigating. Wardle said he couldn’t discuss details of the investigation other than saying he contacted law enforcement. Apple did not respond to multiple requests for comment.
WHODUNNIT?
Neither Reed nor Wardle know how the malware got onto the victim computers. But the big mystery surrounding FruitFly is who is behind it.
The malware doesn’t contain many clues, and it’s not even clear what profile the hackers fit, according to both Wardle and Reed.
FruitFly doesn’t seem made by a nation-state because it’s not sophisticated enough, and it doesn’t appear to be targeting high-profile victims.
Malwarebytes saw it in four computers belonging to research facilities, but the victims Wardle identified run the whole gamut. There’s a few research facilities, but mostly it’s average people, and 90 percent of them are from either US or Canada, according to Wardle.
“Just because they have a Mac, it doesn’t mean that they’re safe.”
Despite targeting regular people, it doesn’t seem to be made by people specifically interested in extorting victims with ransomware or stealing their credit cards and passwords. Wardle said that both versions of FruitFly seemed to be made mostly for surveillance. But FruitFly2they had unusual capabilities such as being able to move the mouse cursor and control the keyboard remotely, and it was programmed to alert the hackers when the computer’s owner returns to control it, according to Wardle. It was also written in Perl, a language that’s “archaic” for malware and used old code, Wardle said.
In other words, the hackers have probably been around for a while, and seem to be neither spies nor cybercriminals.
“[FruitFly] didn’t fit any of those molds,” Wardle said, adding that it seems like it’s a “specific hacker targeting specific individuals” for unknown purposes.
While that shouldn’t cause panic, Wardle said, it is “worrisome.”
“If there are hackers out there who are specifically targeting families or individual Mac users, that kinda makes my stomach turn,” he said. “People need to be really cautious when they use their computers, when their kids use their computers. Just because they have a Mac, it doesn’t mean that they’re safe.”
Wardle is going to talk about FruitFly 2 at the upcoming Black Hat and Def Con conferences in Las Vegas this week.
Correction: a previous version of this story stated that law enforcement is investigating the case, but that’s not confirmed yet, as the FBI declined to comment.
Got a tip? You can contact this reporter securely on Signal at +1 917 257 1382, OTR chat at lorenzo@jabber.ccc.de, or email lorenzo@motherboard.tv
Get six of our favorite Motherboard stories every day by signing up for our newsletter.




